Deploy Nginx Ingress and Cert Manager on a GKE Cluster using Terraform
Terraform has become my go-to IaC tool because it’s AWESOME! and can be used to interact with a lot of API popular tools and services via their API. In this post, I will be sharing a terraform module that will create a GKE Cluster with 3 Nodes and then deploy Nginx Ingress, Cert-Manager, and a sample Wordpress deployment using the Terraform Kubernetes and Helm Providers.
Nginx Ingress is an Ingress controller for Kubernetes using NGINX as a reverse proxy and load balancer.
Cert-Manager is a Kubernetes certificate management controller that can help with issuing certificates from a variety of sources, such as Let’s Encrypt, Hashicorp Vault, Venafi, a simple signing key pair, or a self signed Certificate. One of the benefits is that it will ensure certificates are valid and up to date, and attempt to renew certificates before they expire.
You can access the module on my GitHub . The module includes a terraform.tfvars file that can be modified to create a public GKE Cluster that restricts access by whitelisting any IPs specified in the master_authorized_networks_config variable.
To use the module,
Clone my GitHub repository and switch to the
GKE_Cluster_with_Nginx_Ingressdirectory.Install the latest version of the Terraform CLI as long as it’s newer than 0.12.25 the module will work. As a best practice, I utilize Terraform Workspaces, by creating a workspace per environment. The module requires a workspace to be created in order to create any of the specified resources, to create a workspace run:
terraform workspace new <environment_name>e.g.terraform workspace new devOnce, you’ve created a workspace, you can initialize:
terraform initGenerate an execution plan to ensure the resources match your expectations:
terraform planIf you’re happy with the output, run the apply command to create the resources:
terraform apply -auto-approve
Once the cluster and deployments have been created successfully, terraform will provide outputs that can be used to access the cluster.
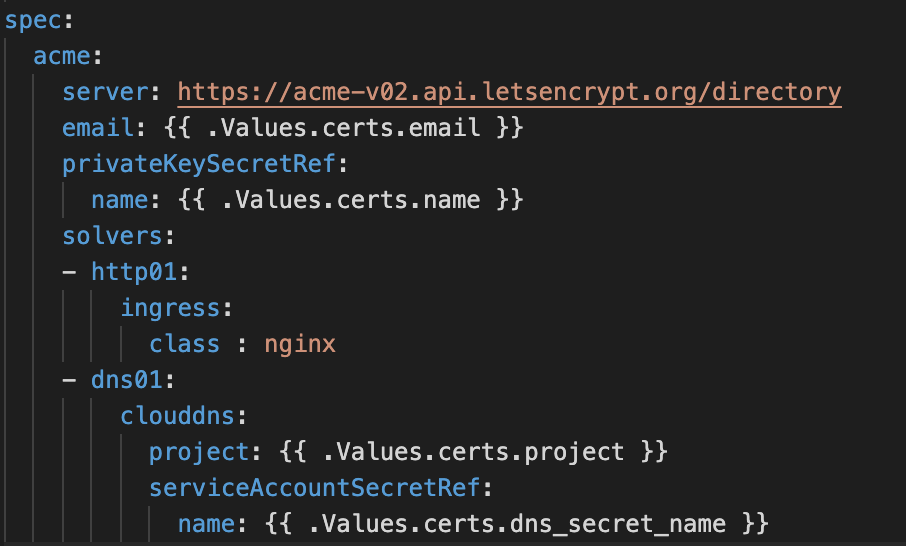
The ingress module will deploy nginx-ingress using the helm provider, it will also deploy the cert-manager chart from the jetstack.io repository and create a ClusterIssuer using a local helm chart. The ClusterIssuer has two solvers specified - http01 and dns01. To use the dns01 provider, you must already have a domain configured using Google CloudDNS. You can learn more about the Let’s Encrypt challenge types here.
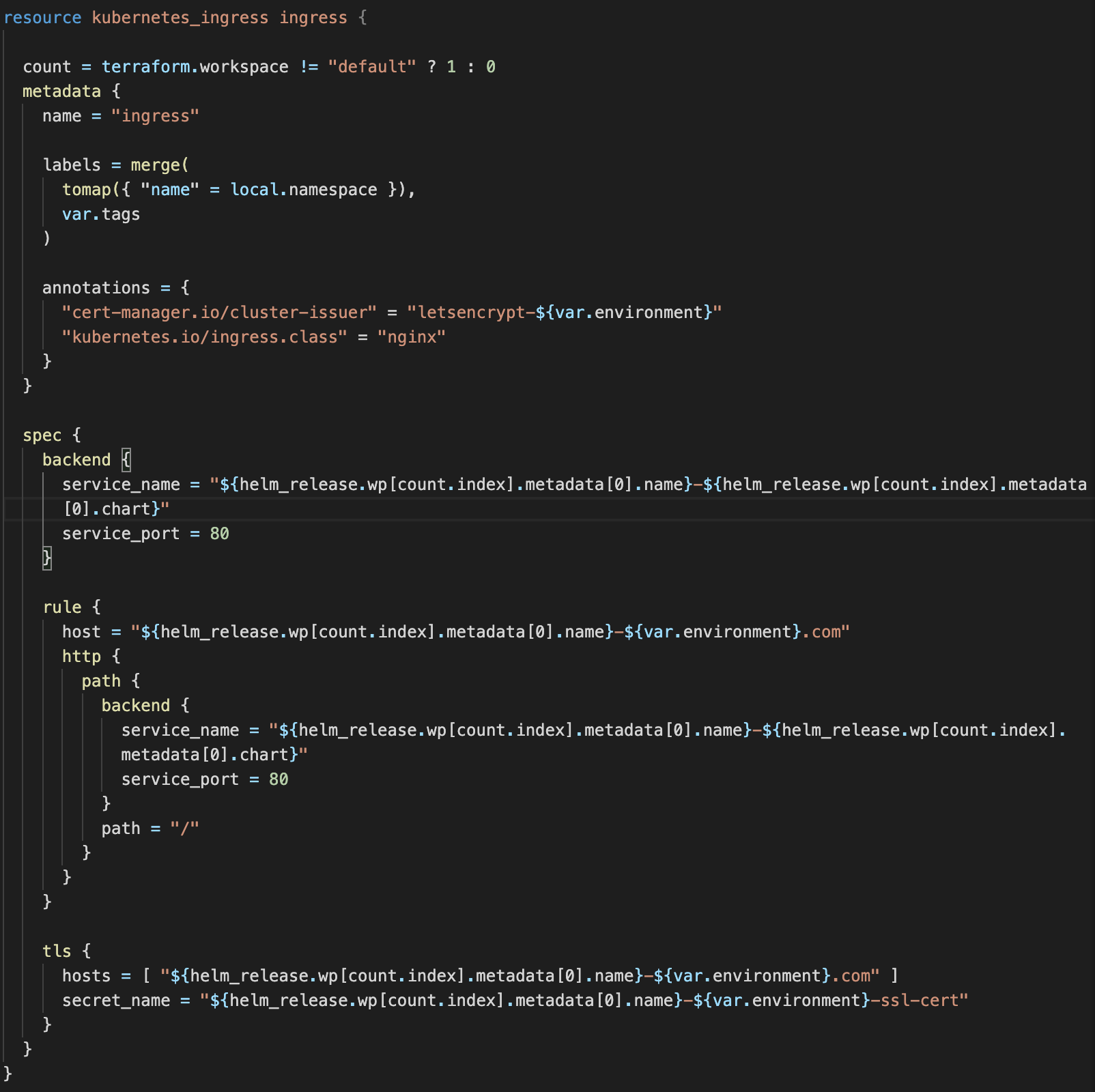
The http01 solver will create/issue certificates automatically when a Kubernetes Ingress resource is created with annotations specifying the ClusterIssuer and the tls block:
The http01 solver will attempt to validate that you control the domain names in the certificate, so be sure to update the module with the appropriate values that correspond with your domain name.
The dns01 solver will attempt to use the specified DNS Provider (Google Cloud DNS in our case) to validate the certificate hosts(domain) and issue the certificate by solving the DNS01 ACME challenge.
*Cover Images from dev.to